Difference between revisions of "TURMOIL"
From Buggedplanet.info
Jump to navigationJump to search (Created page with "= Articles = {|border=1 |- |Date||Source||Title||Tags |- |20120313||williamaarkin. wordpress.com||[http://williamaarkin.wordpress.com/2012/03/13/nsa-code-names-revealed/ NSA Cod...") |
|||
| (22 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| + | = Details = | ||
| + | |||
| + | * Collection mission system, part of [[TURBULENCE]] system | ||
| + | |||
| + | = Slides leaked 20130905 = | ||
| + | |||
| + | <gallery> | ||
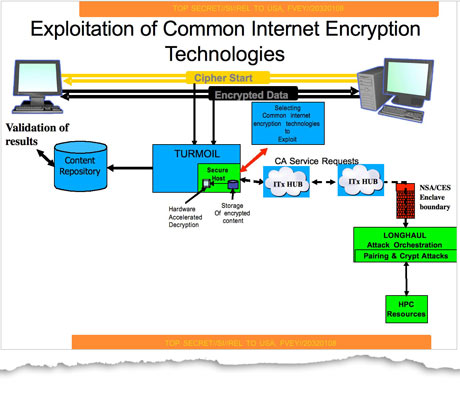
| + | File:20130905-tg-crypto-exploit.jpg|Exploitation of Common Internet Encryption Technologies | ||
| + | </gallery> | ||
| + | |||
= Articles = | = Articles = | ||
| Line 5: | Line 15: | ||
|Date||Source||Title||Tags | |Date||Source||Title||Tags | ||
|- | |- | ||
| − | |20120313||williamaarkin. wordpress.com||[http://williamaarkin.wordpress.com/2012/03/13/nsa-code-names-revealed/ NSA Code Names Revealed]||[[AGILEVIEW]] | + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35536.pdf NSA Document: SCARLETFEVER ]||[[NSA]] / [[TURMOIL]] / [[WEALTHYCLUSTER]] / [[TEe]] / [[SCARLETFEVER]] / [[SSL/TLS]] / [[CRYPTANALYTICS]] |
| + | |- | ||
| + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35534.pdf NSA Document: Net Defense from Encrypted Communications]||[[NSA]] / [[TURMOIL]] / [[BLUESNORT]] / [[GALLANTWAVE]] / [[XKEYSCORE]] / [[LONGHAUL]] / [[NETFLOW]] / [[FULL SNORT]] / [[POPQUIZ]] / [[TUTELAGE]] / [[CRYPTANALYTICS]] | ||
| + | |- | ||
| + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35513.pdf NSA Document: TURMOIL/APEX/APEX High Level Describtion Document]||[[NSA]] / [[APEX]] / [[TURMOIL]] / [[FASHIONCLEFT]] / [[HAMMERMILL]] / [[HAMMERSTEIN]] / [[HAMMERCHANT]] / [[IPSEC]] / [[VPN]] / [[VOIP]] / [[CRYPTANALYTICS]] | ||
| + | |- | ||
| + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35519.pdf NSA Document: POISENNUT Virtual Private Network Attack Orchestrator (VAO)]||[[NSA]] / [[WEALTHYCLUSTER]] / [[POISENNUT]] / [[TURMOIL]] / [[VPN]] / [[CRYPTANALYTICS]] | ||
| + | |- | ||
| + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35525.pdf NSA Document: TURMOIL GALLANTWAVE]||[[NSA]] / [[TURMOIL]] / [[GALLANTWAVE]] / [[VPN]] / [[CRYPTANALYTICS]] | ||
| + | |- | ||
| + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35526.pdf NSA Document: TURMOIL VPN PROCESSING]||[[NSA]] / [[TURMOIL]] / [[VPN]] / [[CRYPTANALYTICS]] | ||
| + | |- | ||
| + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35517.pdf NSA Document: VALIANTSURF (VS) Capabilities]||[[NSA]] / [[TURMOIL]] / [[VALIANTSURF]] / [[CRYPTANALYTICS]] / [[VPN]] | ||
| + | |- | ||
| + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35518.pdf NSA Document: VS MALIBU IKE and ESP Metadata Flows]||[[NSA]] / [[MALIBU]] / [[TURMOIL]] / [[VALIANTSURF]] / [[VPN]] / [[CRYPTANALYTICS]] | ||
| + | |- | ||
| + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35528.pdf NSA Document: SPIN 15 VPN Story]||[[NSA]] / [[TURMOIL]] / [[VPN]] / [[CRYPTANALYTICS]] | ||
| + | |- | ||
| + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35526.pdf NSA Document: TURMOIL IPSEC VPN Sessionization]||[[NSA]] / [[TURMOIL]] / [[IPSEC]] / [[VPN]] / [[CRYPTANALYTICS]] | ||
| + | |- | ||
| + | |20141228||spiegel.de||[http://www.spiegel.de/media/media-35529.pdf NSA Document: Fielded Capability: End-to-End VPN SPIN 9 Design Review]||[[NSA]] / [[TURBULENCE]] / [[TURMOIL]] / [[PRESSUREWAVE]] / [[TOYGRIPPE]] / [[KEYCARD]] / [[XKEYSCORE]] / [[TUBE]] / [[IPSEC]] / [[VPN]] / [[CRYPTANALYTICS]] | ||
| + | |- | ||
| + | |20140618||spiegel.de||[http://www.spiegel.de/media/media-34025.pdf NSA Document: German, NSA SIGINTers Share DNI Processing Knowledge]||[[BND]] / [[NSA]] / [[DE]] / [[JSA]] / [[GRANDMASTER]] / [[WEALTHYCLUSTER]] / [[TURMOIL]] / [[BLACKNIGHT]] / [[DNI]] | ||
| + | |- | ||
| + | |20131230||spiegel.de||[http://www.spiegel.de/netzwelt/netzpolitik/quantumtheory-wie-die-nsa-weltweit-rechner-hackt-a-941149.html NSA-Programm Quantumtheory: Wie der US-Geheimdienst weltweit Rechner knackt]||[[NSA]] / [[QUANTUMTHEORY]] / [[QUANTUMBOT]] / [[QUANTUMCOPPER]] / [[TAO]] / [[QFIRE]] / [[TURBULENCE]] / [[TURMOIL]] / [[TURBINE]] / [[TUTELAGE]] / [[QUANTUMSKY]] / [[QUANTUM INSERT]] / [[SCS]] / [[STRAIGHTBIZARRE]] / [[BLINDDATE]] | ||
| + | |- | ||
| + | |20131004||theguardian.com||[http://www.theguardian.com/world/2013/oct/04/tor-attacks-nsa-users-online-anonymity Attacking Tor: how the NSA targets users' online anonymity - Secret servers and a privileged position on the internet's backbone used to identify users and attack target computers]||[[NSA]] / [[STORMBREW]] / [[FAIRVIEW]] / [[OAKSTAR]] / [[BLARNEY]] / [[XKEYSCORE]] / [[TURBULENCE]] / [[TURMOIL]] / [[TUMULT]] / [[FOXACID]] / [[QUANTUM]] / [[TAO]] / [[EGOTISTICALGIRAFFE]] / [[FRUGALSHOT]] | ||
| + | |- | ||
| + | |20130906||theguardian.com||[http://www.theguardian.com/world/2013/sep/05/nsa-gchq-encryption-codes-security Revealed: how US and UK spy agencies defeat internet privacy and security]||[[NSA]] / [[GCHQ]] / [[TURMOIL]] / [[LONGHAUL]] / [[BULLRUN]] | ||
| + | |- | ||
| + | |20120313||williamaarkin. wordpress.com||[http://williamaarkin.wordpress.com/2012/03/13/nsa-code-names-revealed/ NSA Code Names Revealed]||[[AGILEVIEW]] / [[AGILITY]] / [[AIRGAP]] / [[COZEN]] / [[AIGHANDLER]] / [[ANCHORY]] / [[MAUI]] / [[ARCANAPUP]] / [[ARTEMIS]] / [[ASSOCIATION]] / [[AUTOSOURCE]] / [[BEAMER]] / [[BELLVIEW]] / [[BLACKPEARL]] / [[CADENCE]] / [[GAMUT]] / [[CHALKFUN]] / [[CINEPLEX]] / [[CLOUD]] / [[COASTLINE]] / [[COMMONVIEW]] / [[CONTRAOCTAVE]] / [[COURIERSKILL]] / [[CREEK]] / [[CREST]] / [[CROSSBONES]] / [[CPE]] / [[CULTWEAVE]] / [[CYBERTRANS]] / [[DISHFIRE]] / [[DOUBLEARROW]] / [[DRAGONFLY]] / [[WEALTHYCLUSTER (EWC)]] / [[ETHERREAL]] / [[FASCIA]] / [[FASTSCOPE]] / [[FOREMAN]] / [[GAMUT/UTT]] / [[GISTQUEUE]] / [[GJALLER]] / [[GLAVE]] / [[GLOBALREACH]] / [[GOLDMINER]] / [[GOLDPOINT]] / [[GOSSAMER]] / [[GROWLER]] / [[HERCULES]] / [[HIGHTIDE]] / [[SKYWRITER]] / [[HOMEBASE]] / [[INFOSHARE]] / [[JOLLYROGER]] / [[KINGFISH]] / [[LIQUIDFIRE]] / [[MAINWAY]] / [[MARINA]] / [[MASTERLINK]] / [[MASTERSHAKE]] / [[MESSIAH]] / [[METTLESOME]] / [[NEWHORIZONS]] / [[NIGHTSURF]] / [[NORMALRUN]] / [[CHEWSTICK]] / [[FALLENORACLE]] / [[NUCLEON]] / [[OCTAVE]] / [[PATHMASTER]] / [[MAILORDER]] / [[PINWALE]] / [[PANOPTICON]] / [[PRESENTER]] / [[PROTON]] / [[RAVENWING]] / [[RENOIR]] / [[ROADBED]] / [[SCORPIOFORE]] / [[SHARKFINN]] / [[SKOPE]] / [[SNAPE]] / [[SPOTBEAM]] / [[STINGRAY]] / [[SURREY]] / [[TAPERLAY]] / [[TAROTCARD]] / [[TEMPTRESS]] / [[TRACFIN]] / [[TRAILMAPPER]] / [[TREASUREMAP]] / [[TRICKLER]] / [[TUNINGFORK]] / [[SEEKER]] / [[TURMOIL]] / [[TUSKATTIRE]] / [[TWISTEDPATH]] / [[UIS]] / [[UTT]] / [[WEALTHYCLUSTER]] / [[WIRESHARK]] / [[WITCHHUNT]] / [[XKEYSCORE]] / [[YELLOWSTONE/SPLITGLASS]] | ||
|- | |- | ||
|} | |} | ||
| − | [[Category:NSA programs]] | + | [[Category:NSA programs]] [[Category:Cryptanalysis and Exploitation Services (CES)]] |
Latest revision as of 16:44, 30 December 2014
Details
- Collection mission system, part of TURBULENCE system