Difference between revisions of "FAIRVIEW"
From Buggedplanet.info
Jump to navigationJump to search| Line 17: | Line 17: | ||
|- | |- | ||
|Date||Source||Title||Tags | |Date||Source||Title||Tags | ||
| + | |- | ||
| + | |20131211||cryptome.org||[http://cryptome.org/2013/12/nsa-ghost-machine.pdf NSA GHOSTMACHINE (Belated)]||[[SSO]] / [[GHOSTMACHINE]] / [[US-3127]] / [[US-3145]] / [[US-3167]] / [[US-3180]] / [[US-3190]] / [[US-3237]] / [[US-3261]] / [[US-3273]] / [[US-3293]] / [[US-3300]] / [[US-3311]] / [[US-983]] / [[US-990]] | ||
|- | |- | ||
|20131004||theguardian.com||[http://www.theguardian.com/world/2013/oct/04/tor-attacks-nsa-users-online-anonymity Attacking Tor: how the NSA targets users' online anonymity - Secret servers and a privileged position on the internet's backbone used to identify users and attack target computers]||[[NSA]] / [[STORMBREW]] / [[FAIRVIEW]] / [[OAKSTAR]] / [[BLARNEY]] / [[XKEYSCORE]] / [[TURBULENCE]] / [[TURMOIL]] / [[TUMULT]] / [[FOXACID]] / [[QUANTUM]] / [[TAO]] / [[EGOTISTICALGIRAFFE]] / [[FRUGALSHOT]] | |20131004||theguardian.com||[http://www.theguardian.com/world/2013/oct/04/tor-attacks-nsa-users-online-anonymity Attacking Tor: how the NSA targets users' online anonymity - Secret servers and a privileged position on the internet's backbone used to identify users and attack target computers]||[[NSA]] / [[STORMBREW]] / [[FAIRVIEW]] / [[OAKSTAR]] / [[BLARNEY]] / [[XKEYSCORE]] / [[TURBULENCE]] / [[TURMOIL]] / [[TUMULT]] / [[FOXACID]] / [[QUANTUM]] / [[TAO]] / [[EGOTISTICALGIRAFFE]] / [[FRUGALSHOT]] | ||
Revision as of 06:09, 23 December 2013
Details
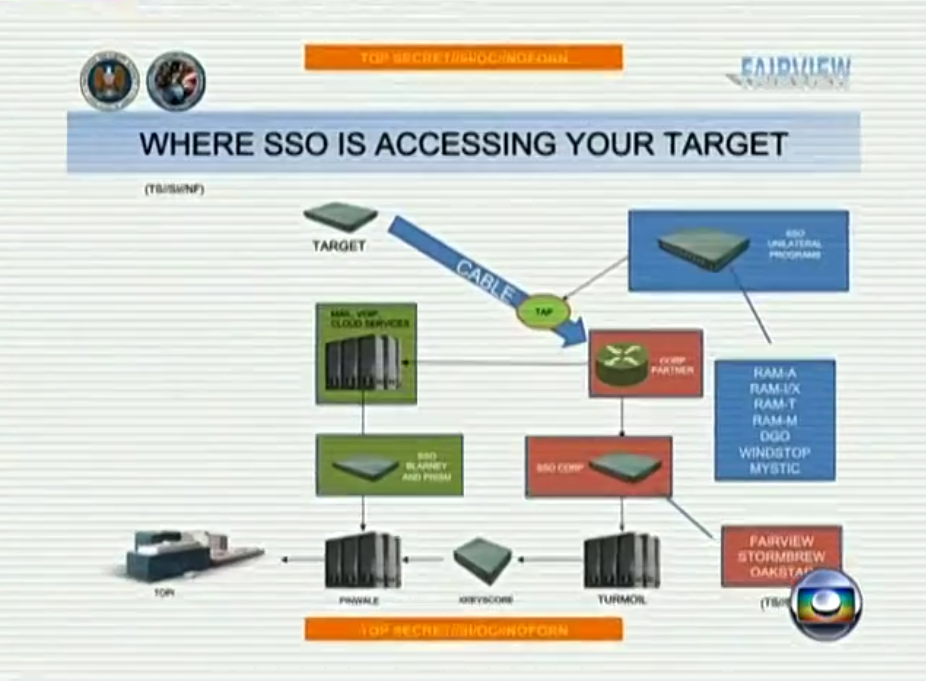
Collection fo communications on fiber cables and infrastructure as data flows past.
Part of UPSTREAM